Prisma Access is based on Palo Alto Networks PAN-OS software, which allows your organization to add capabilities to your Prisma Access network deployment without deploying additional equipment. You can enable enhanced threat-prevention services, network-interconnect and service-connection options, data loss prevention services, and IoT device security services.
SaaS Security Inline
The Prisma Access SaaS Security Inline service add-on provides SaaS application visibility, control, and advanced analytics to help organizations manage data-security risks. It uses cloud-based machine learning to discover and classify SaaS applications, offering insights into sanctioned and unsanctioned usage. This solution enables complete control over SaaS application use from corporate networks and managed devices traversing Prisma Access, seamlessly integrating with existing security systems.
The Palo Alto Networks SaaS Security portfolio combines API-based and inline services to deliver comprehensive CASB (Cloud Access Security Broker) capabilities without requiring network reconfiguration, probes, or endpoint configurations. A critical component is the Strata Logging Service (SLS), which logs traffic-flow information and scans it for SaaS application access. The SaaS Security database, with over 15,000 SaaS application IDs, uses machine learning to classify new or unknown applications, enhancing visibility and enabling risk analysis.
Prisma Access leverages the PAN-OS-based App-ID engine to identify applications across all ports and protocols, even for encrypted or tunneled traffic. It enables security policy configuration to control SaaS access based on App-IDs, URL matches, IP ranges, and user identities, ensuring robust application management and security.
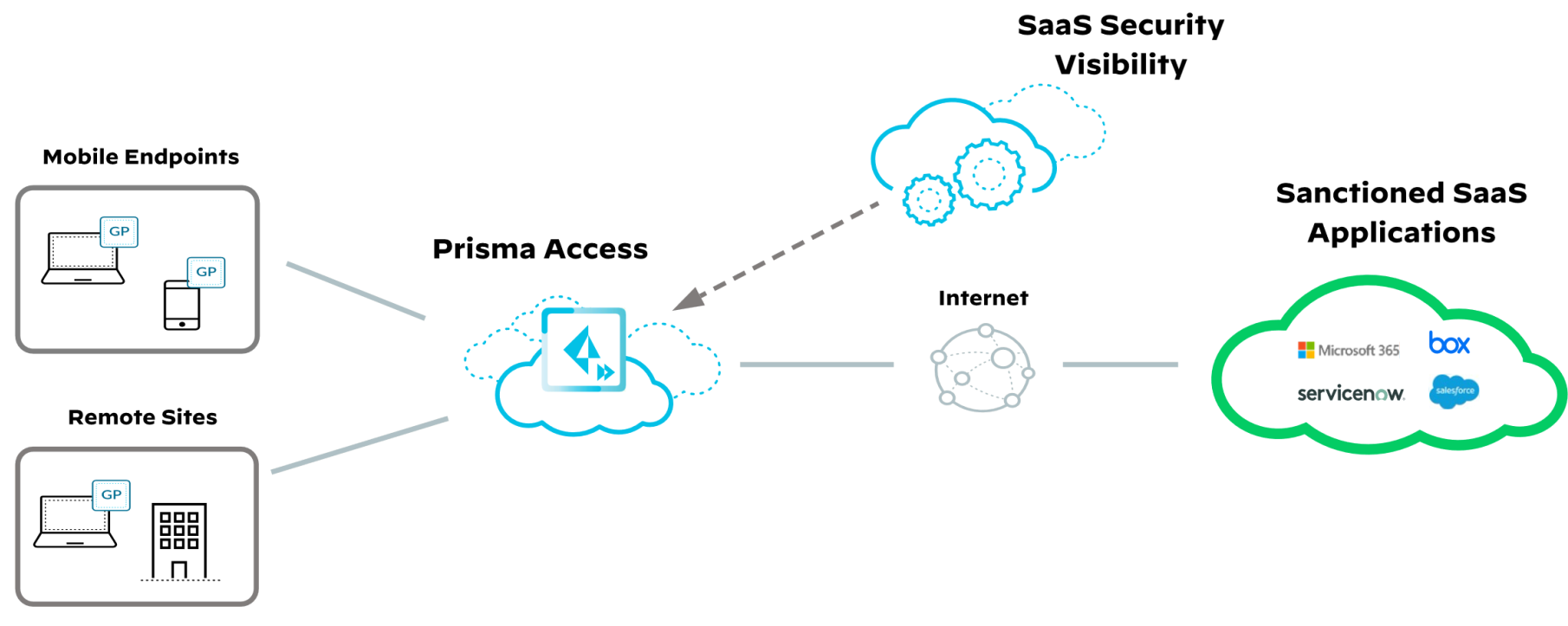
SaaS Security Inline visibility is delivered as a SaaS service, so no footprint is required in the data center. The single SaaS Security management application monitors and controls both in-line and API-based SaaS visibility and control. Because SaaS Security provides visibility into stored data and historical activities, you can explore and investigate them on-demand. The SaaS Security API (formerly known as Prisma SaaS) is licensed separately from SaaS Security Inline for Prisma Access.
Data Loss Prevention
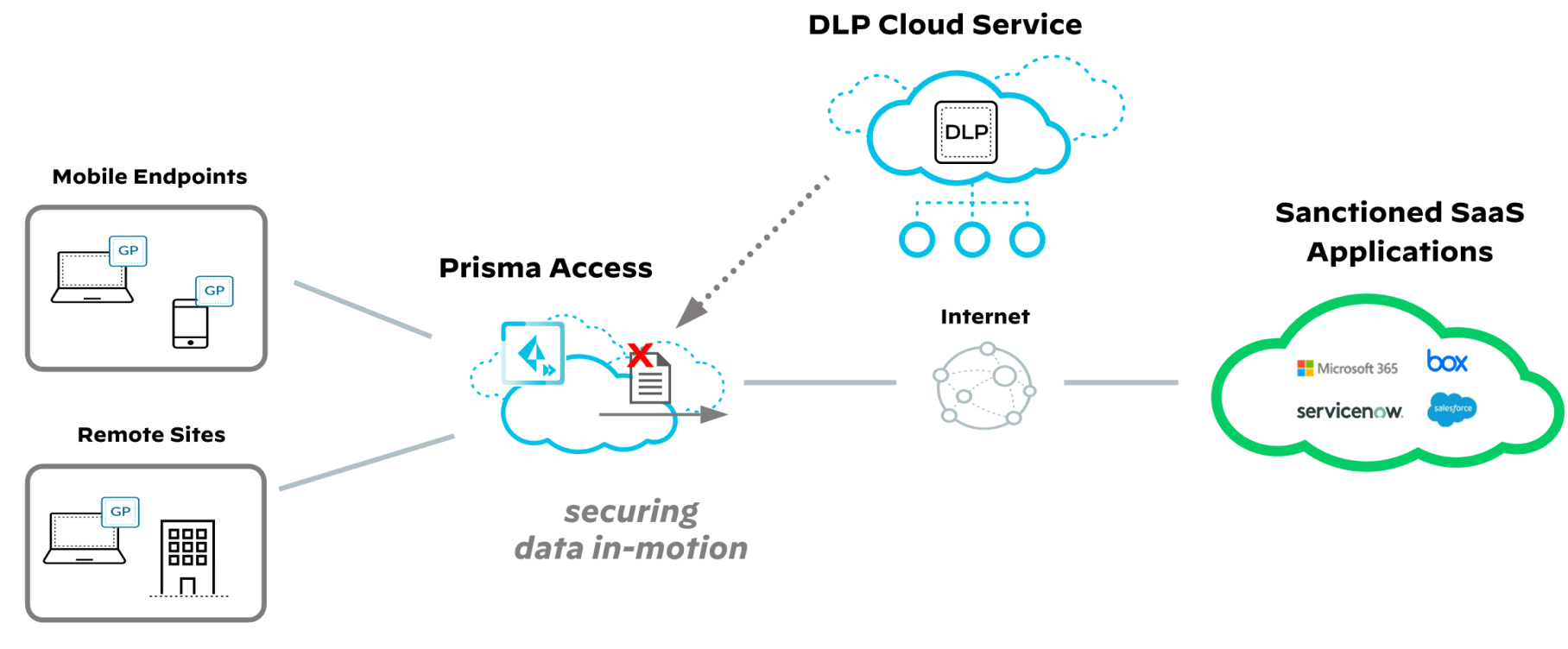
Data Loss Prevention (DLP) is a cloud-delivered solution that protects sensitive data from breaches, regulatory violations, and misuse. Initially available only for SaaS Security via API-based scans, DLP now offers unified detection policies embedded in existing control points for visibility and enforcement across the cloud (via Prisma Access) and on-premises (via NGFW).
With Prisma Access, DLP provides real-time visibility into data-in-motion and enforces data distribution policies. It prevents data leaks to unsanctioned apps or uploads to corporate apps through advanced inline analysis. The solution offers unified policies and faster remediation for comprehensive enterprise data protection.
Remote Browser Isolation
Remote Browser Isolation (RBI) is a service that isolates and transfers all browsing activity from the user’s managed devices and corporate networks to an outside entity, such as Prisma Access, that secures and isolates potentially malicious code and content within the platform. Natively integrated with Prisma Access, Palo Alto Networks RBI allows you to apply isolation profiles easily to existing security policies. To keep sensitive data and information secure, isolation profiles restrict many user controls, such as copy-and-paste actions, keyboard inputs, and sharing options such as uploading, downloading, and printing files,.
RBI works by creating a no-code execution isolation channel between users and the browser, which mitigates zero-day web threats by never allowing malicious files to execute on a user’s machine. Unlike other isolation solutions, the Palo Alto Networks RBI solution uses next-generation isolation technologies to deliver near-native experiences for users accessing websites—without compromising on security.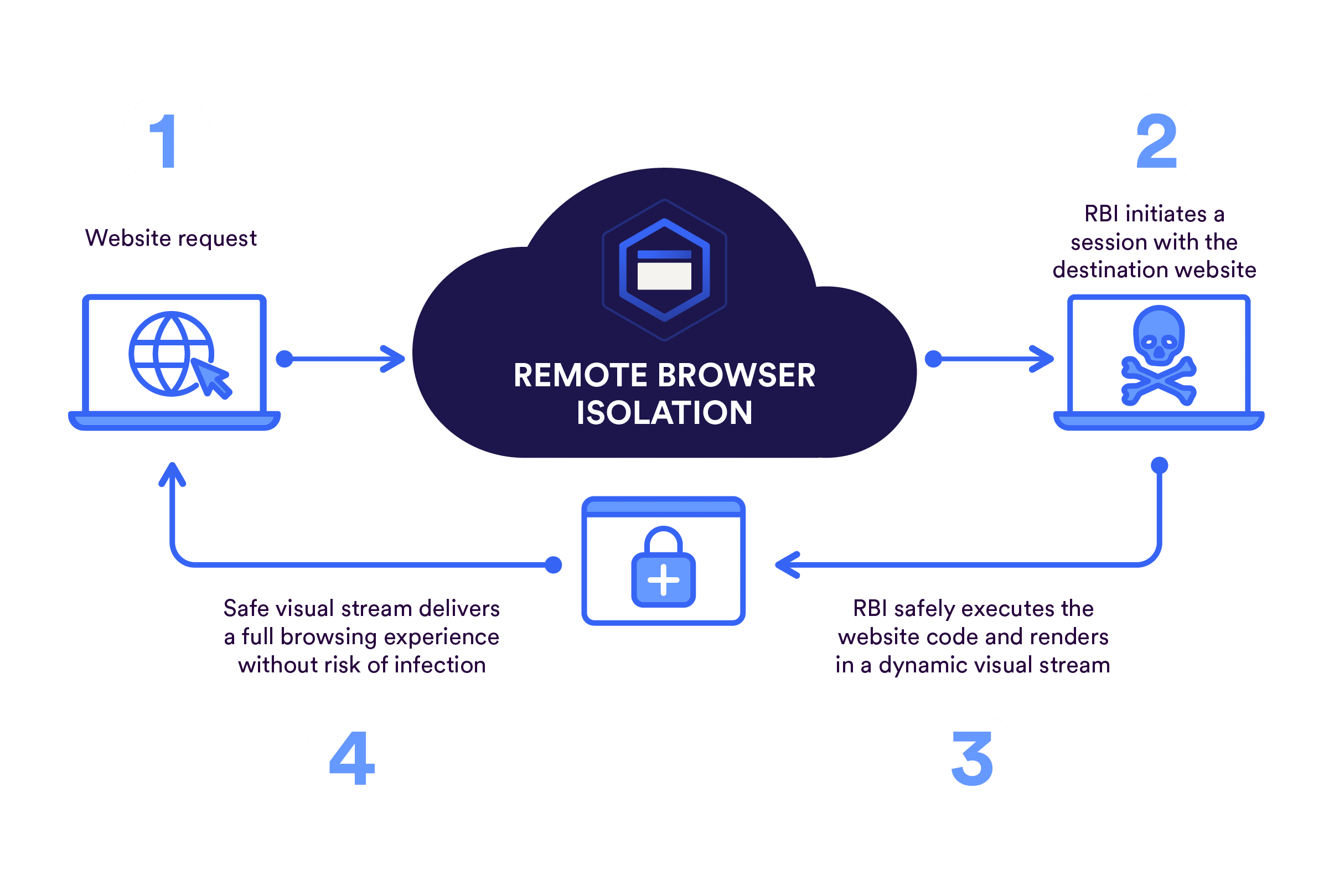 App Acceleration
App Acceleration
App Acceleration enhances TCP-based application performance by up to five times compared to direct internet traffic, without requiring changes to user clients or applications. It predicts user actions, preloads dynamic content, and processes security tasks in advance, ensuring content is ready when requested.
It optimizes TCP performance through aggressive window tuning, real-time custom packet flow profiles, and adjustments for conditions like packet loss, jitter, and corruption. By considering network, device, and application context, App Acceleration maximizes data delivery efficiency for a seamless user experience.
Autonomous Digital Experience Management
Autonomous Digital Experience Management (ADEM) is an add-on service providing end-to-end visibility of the service delivery path to monitor user application experiences. It operates in two modes:
- ADEM for Mobile Users: Integrated into the GlobalProtect app, requiring no additional software or appliances, it activates based on Prisma Access policies.
- ADEM for Remote Networks: Built into Prisma SD-WAN ION devices at remote sites connected to Prisma Access for secure internet access.
ADEM continuously monitors every segment from the endpoint to the application, establishing baseline metrics and detecting performance issues across endpoints, Wi-Fi, LAN, routers, ISPs, Prisma Access, and applications (SaaS, IaaS, or data centers). It simplifies troubleshooting by isolating problem segments and offering remediation insights or self-remediation recommendations.
Key features include:
- User Traffic Visibility: Tracks real traffic to SaaS, IaaS, internet-based, and data center applications.
- Synthetic Monitoring: Uses tests to measure network and application performance metrics (e.g., latency, jitter, DNS resolution, time to first/last byte).
- Endpoint Monitoring: For mobile users, the GlobalProtect app collects device health and Wi-Fi telemetry to identify performance issues caused by the endpoint or connectivity.
AI-Powered Autonomous Digital Experience Management
AI-Powered ADEM integrates AIOps with ADEM, using AI and machine learning to identify patterns, detect anomalies, correlate events, and generate alerts. It leverages anonymized, crowdsourced data to provide insights, such as detecting ISP issues in specific regions and raising incidents for proactive resolution.
Enabled by default with an activated AIOps license, it enriches ADEM data with advanced AI/ML models and requires no additional configuration. Its capabilities apply to both mobile users and remote networks.
Key features include:
- Proactive Monitoring: Runs synthetic tests to monitor the health of users, applications, and remote sites.
- Anomaly Detection: Collects baseline data to identify network anomalies.
- Capacity Forecasting: Generates reports to forecast bandwidth requirements for remote networks.
Advanced Troubleshooting: Uses Access Analyzer for complex queries, assisting with identifying and resolving specific user or application issues.
Traffic Replication
On-premises network recorders have been a powerful tool when organizations perform forensic and breach analysis. It is common in on-premises topologies to implement a parallel infrastructure of TAP ports, SPAN ports, or packet brokers that would deliver a copy of the traffic to be used for such out-of-band analysis. Prisma Access Traffic Replication brings this functionality to SASE. The Traffic Replication add-on is licensed on a per-user basis for both mobile users and remote networks.
Traffic Replication uses the Prisma Access cloud to replicate traffic from Prisma Access and forward them to Google Cloud storage buckets that you or third-party nodes can access for analysis. To reduce risk and keep your organization safe, Traffic Replication provides access to packet captures of users’ real-world traffic, thereby enabling the detection and remediation of threats that could span multiple sessions or the identification and response to anomalous behaviors.
In the upcoming post, I’ll begin diving into the details of Prisma Access design, exploring its management options and key components, see you soon!