DDoS (distributed denial of service) attacks pose a significant and ongoing threat to all networks, this series explores six well-established technologies and architectures you can use to safeguard your assets.
- Overprovisioning
- DDoS Mitigation Appliances
- ISP Scrubbers
- Third-Party Scrubbing Services
- Cloud Web Application Firewall
- Blackholing
A common initial response by organizations facing the threat of DDoS attacks is to enhance the resiliency of their data centers, two well-established and widely-used DDoS mitigation technologies are available for on-premises protection, these solutions can be effective against small to medium-sized attacks but may struggle with larger-scale assaults due to capacity limitations.
Overprovisioning
This approach increases network capacity by provisioning critical resources—such as web and email hosting, servers, and network connections—at 40-60% of normal usage instead of the more typical 80% utilization. It is straightforward to implement without requiring specialized security expertise and leverages the DDoS mitigation features built into network equipment like routers, firewalls, and intrusion detection systems (IDS). However, it necessitates the overprovisioning of many additional network components, including backend databases, web and email servers, application servers, firewalls, and network switches.
Organizations that also utilize cloud resources can take advantage of cloud autoscaling to rapidly and significantly enhance mitigation capacity, enabling the overprovisioned infrastructure to withstand larger attacks. However, autoscaling can lead to higher usage and increased costs.
The main limitation of this strategy is its restricted capacity, especially as DDoS attacks continue to grow in size and intensity. Nonetheless, it remains effective against smaller, more common attacks.
Anti-DDoS Appliances
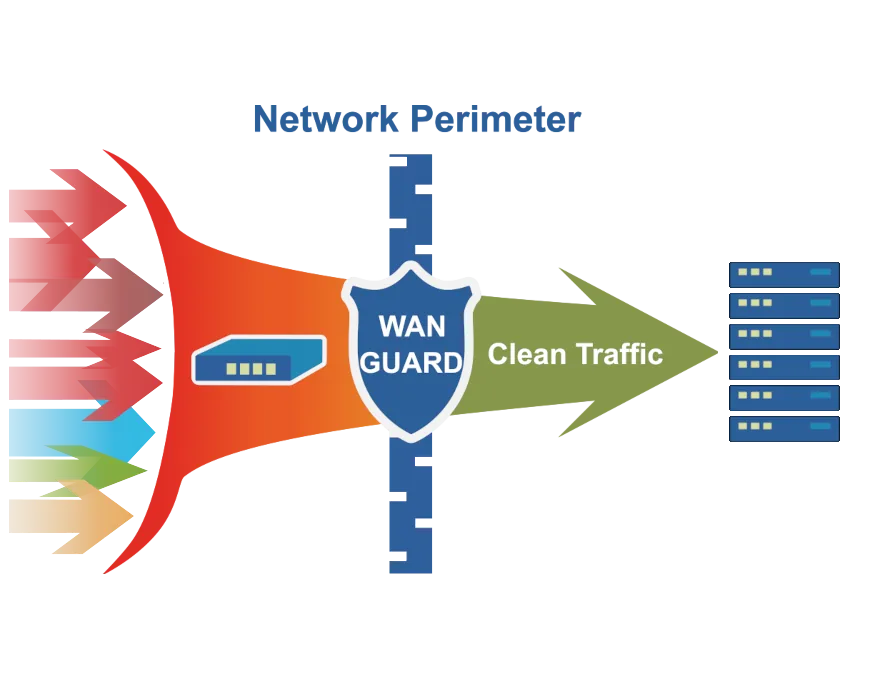
This technology employs specialized appliances in the data center, specifically designed to counter DDoS attacks. These devices function as high-capacity intrusion detection systems (IDS) that can effectively identify and filter out DDoS traffic.
The appliances operate by rapidly detecting distinct DDoS traffic patterns and immediately dropping the malicious traffic. They should be positioned upstream of the firewalls and routers in the data center. Multiple appliances can be deployed together to increase mitigation capacity, effectively creating an in-house DDoS scrubbing center.
Each data center requires its own appliance(s), leading to potentially high costs for larger organizations. Additionally, these appliances need regular updates or replacements, contributing to ongoing capital expenses. Implementing this technology also necessitates some IT engineering involvement, ideally with staff knowledgeable in DDoS mitigation to monitor and respond to attacks.
For organizations able to meet these requirements, mitigation appliances can successfully manage the frequent small-scale DDoS attacks and, when deployed in multiple units, can also handle moderate attacks. However, the effectiveness of these appliances is ultimately limited by the bandwidth of the circuits from your ISPs. An attack that exceeds this bandwidth can overwhelm your network before it reaches the mitigation appliances, resulting in downtime.
DDoS mitigation appliances can also be deployed at an ISP or third-party scrubbing center, upstream from the data center. The next post in this series will discuss ISP scrubbing centers.
ISP Scrubbers
The first two techniques covered on-premises solutions for DDoS mitigation within the datacenter. The third solution moves upstream from the datacenter and discusses a technology with considerably larger capacity: ISP scrubbing centers.
In this solution, you work with your ISP(s) to route traffic for specific IP addresses through scrubber appliances within their network. These appliances filter the traffic before forwarding it to your datacenter(s).
An ISP scrubbing center is a highly effective and relatively easy solution to implement, as your ISPs are already your service providers. It offers significantly greater capacity than on-premises technologies, and mitigation can be quickly activated since your traffic is already routed through the ISP. In most cases, the ISP can route entire network blocks or individual IP addresses to their scrubbing appliances and return clean traffic.
However, ISP scrubbing capacity has its limits, typically ranging from 20 to 120 Gbps, based on their available peering bandwidth. If an attack exceeds this capacity, it can overwhelm the ISP’s peering connections and degrade service for other customers. In such cases, the ISP may be forced to divert traffic, often to a remotely triggered black hole, cutting off access to your site entirely.
For businesses using multiple ISPs, separate contracts are required with each provider, increasing both costs and complexity. Additionally, if an attack slips through one of your ISPs, your public-facing services may be disrupted, even if other ISPs are successfully scrubbing traffic. A comprehensive DDoS mitigation strategy typically involves multiple layers of protection using different technologies.