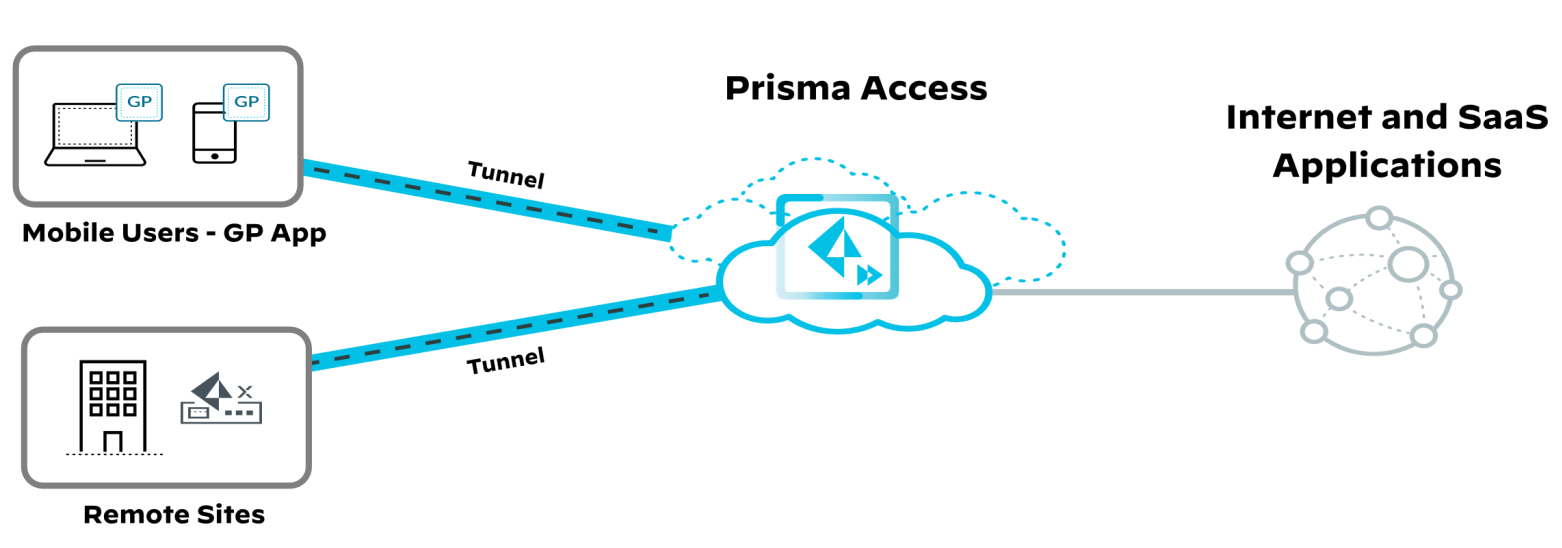
Prisma Access ensures consistent application visibility and control for all users, regardless of location. It secures traffic from mobile endpoints to SaaS applications, preventing direct, unsecured access.
Beyond internet access, Prisma Access provides secure transport for enterprise traffic between remote offices, mobile users, and data center applications. Its global backbone connects over 100 secure access locations, using VPN technology to ensure secure and isolated traffic. Organizations can customize traffic transport over this backbone based on licensing options.
Prisma Access delivers security services like App-ID and threat prevention for mobile and remote users. Data centers connect via IPSec VPN tunnels from on-premises devices. The service is fully managed by Palo Alto Networks.
Management Options:
You have the following two options for provisioning and managing Prisma Access:
- Cloud-managed (through Strata Cloud Manager)
- Panorama® managed (through the Cloud Services plugin)
Because you cannot switch between them after you have activated your Prisma Access license, you must decide which management interface you plan to use prior to provisioning your Prisma Access network. The two management interfaces have different programming flows and different feature support matrices. Regardless of which management interface you use, Prisma Access uses SLS for log storage and Strata Cloud Manager for comprehensive monitoring, alerting and visibility
Cloud Managed
Cloud Manager simplifies cloud-based management of Prisma Access by providing task-driven workflows for onboarding mobile users and remote networks. It offers a unified interface for managing your entire SASE environment, enabling seamless navigation between Prisma Access, Prisma SD-WAN, and cloud-delivered security services. It also provides direct access to Prisma Access dashboards and logs from Strata Logging Service (SLS).
Key features include:
- Easy Setup: Intuitive workflows with predefined options for quick deployment and testing.
- Internet Access Protection: Integrated security rules block malicious and high-risk websites.
- Threat Prevention: Built-in tools like antivirus, WildFire, and anti-spyware configured with best practices.
- User-ID Distribution: Automatically shares user identity data across the Prisma Access backbone and on-premises firewalls.
- Directory Services Integration: Syncs on-premises LDAP or cloud-based Microsoft Entra ID groups via Cloud Identity Engine.
- IPSec and SSL Setup: Default configurations for common IPSec devices and SSL decryption based on best practices.
Cloud Manager streamlines management, security rule configuration, and operational efficiency for Prisma Access.
Panorama Managed
You manage Prisma Access through the Cloud Services plugin on Panorama. Panorama does not interact with Prisma Access security-processing nodes in the same way it does with the next-generation and VM-Series firewalls in your organization. The Cloud Services plugin provides an abstraction layer between Prisma Access and Panorama, decoupling Panorama from the specifics and versions of the security-processing nodes within Prisma Access. When Palo Alto Networks provides an update for Prisma Access, you might need to update the Cloud Services plugin to get the latest Prisma Access features; however, Panorama itself typically doesn’t require a software update.
You configure network and security policies for Prisma Access by using the Cloud Services plugin for Panorama and Prisma Access-specific templates and device groups. This method of configuration enables you to provide consistent security policy enforcement that meets your organization’s usage guidelines.
Prisma Access Dashboards
Prisma Access dashboards in Cloud Manager offer visibility into the health and performance of your infrastructure. These dashboards are available for all Prisma Access instances and can be accessed even when using Panorama for management.
Key features include:
- Health & Performance Monitoring: Monitors Prisma Access instances, whether managed through Cloud Manager or Panorama.
- Overview Screen: Provides a summary of the entire Prisma Access environment’s health and performance.
- Customizable Alerts: Set notifications to highlight issues or events needing attention.
- Multiple Dashboards: Offers focused views for different deployments, alerts, and infrastructure health.
- Flexible Interfaces: Allows toggling between views and evaluating trends over various timeframes.
- Drill-Down Capabilities: Access detailed information on users, sites, connections, or infrastructure components.
- System Messaging: Includes important updates like upcoming system changes.
These dashboards support comprehensive monitoring, alerting, and visibility for your Prisma Access infrastructure.
Components:
When a mobile or remote-site user connects to a Prisma Access gateway, internet-bound application traffic automatically exits the Prisma Access network at the closest internet access point. You must decide how to provide access to internal and on-premises resources for your mobile users. In Prisma Access, you provide this access by using service connections that pair to an IPSec-capable device, such as a router or a Palo Alto Networks NGFW at your data center or headquarters. You can configure service connections to as many as one hundred sites depending on the licensing you choose.
Strata Logging Service
Prisma Access uses Strata Logging Service (SLS) to store logs and provide centralized cloud-based log aggregation for Prisma Access, Cortex XDR® Agent management, and both on-premises and virtual firewalls. SLS is secure, resilient, and fault-tolerant, and its cloud service delivery allows easy scaling and integration with the hub.
SLS offers public-cloud scalability across multiple secure locations and leverages AI to normalize, analyze, and connect enterprise data to detect security issues. It uses cloud-scale compute resources to apply advanced AI and machine learning across data from Prisma Access and other sources. SLS serves as the primary data repository for Palo Alto Networks’ security applications like Cortex XDR, AutoFocus®, and third-party analytics tools, enabling advanced analytics and enhanced threat prevention.
Mobile-User Connections
Prisma Access provides multiple methods for organizations to connect users to their Prisma Access instance. There are three ways to connect mobile users:
- GlobalProtect app—The mobile user has the GlobalProtect application on their endpoint and connects to the GlobalProtect portal to access the Prisma Access instance for internal, SaaS, and internet applications.
- Explicit-proxy connection method—The mobile users’ web browser is configured to connect to the organizations’ Prisma Access explicit-proxy instance for HTTP or HTTPS access to internet-based SaaS applications.
- Clientless VPN—An organization with unmanaged users who require secured access to selected applications can use Prisma Access to provide secured and controlled access to internal applications.
This guide focuses on the GlobalProtect connection method for managed users, which provides access to internal and internet-based applications.
GlobalProtect Portal
Prisma Access provides the GlobalProtect portal functionality through resilient security-processing nodes deployed globally. The service uses global DNS load-balancing to direct clients to the nearest portal. GlobalProtect portal is a secure web service that provides for the distribution and management of GlobalProtect apps. The portal provides an authenticated SSL web service for the download of the GlobalProtect app to end users for self-service deployment. Once connected, the GlobalProtect app receives configuration information from the portal, including a list of Prisma Access locations, external and internal GlobalProtect gateways, required certificates, connection methods, and app behavior. In addition to app configuration, the portal can also distribute the GlobalProtect app to both macOS and Windows endpoints.
Prisma Access GlobalProtect Gateway Locations
Prisma Access uses gateways to connect mobile users to the organization’s Prisma Access instance. GlobalProtect gateways provide security for traffic from GlobalProtect apps, establishing a secure tunnel via IPSec or SSL.
There are two types of GlobalProtect gateways:
- Internal Gateway: Located within the organization’s network, this gateway can be a dedicated or multi-function device. It works with User-ID and host information profile (HIP) checks to authenticate users and map users to IPs and device states. It typically operates in non-tunnel mode, capturing and sharing user data with other firewalls for policy enforcement.
- External Gateway: Located outside the organization’s network, it provides security for mobile users’ traffic to the internet and internal services. GlobalProtect apps tunnel traffic to this gateway via IPSec or SSL.
Prisma Access provides external gateway functionality globally, with the ability to choose locations for close distribution to mobile users. The configuration remains simple regardless of location count. If there are pre-existing GlobalProtect gateways, mobile users can connect to both Prisma Access and those external gateways. Internal gateway functionality is not available within Prisma Access, but the app can connect to external internal gateways for on-site users while still gathering user-to-IP mappings.
GlobalProtect App
The GlobalProtect app runs on Windows, macOS, Linux, iOS, Android, and Chrome. The GlobalProtect app is responsible for connecting to Prisma Access to obtain configuration information and then choosing a Prisma Access location to which it authenticates and tunnels traffic. When users connect, the GlobalProtect app supplies User-IDs and device information .
Also, if required, the GlobalProtect app inventories the endpoint configuration and builds an HIP to share with Prisma Access or an internal gateway. You can use this information to build HIP-based policies based on several attributes, including the following:
- Operating system and application patch level.
- Host anti-malware/firewall version and state.
- Customized host conditions (examples: registry entries, running software).
In the upcoming post, we will dive deeper into the building blocks of the SASE access infrastructure, exploring how security processing nodes play a central role in the Prisma Access virtual infrastructure.